 |
市場調查報告書
商品編碼
1443943
端點安全:市場佔有率分析、產業趨勢與統計、成長預測(2024-2029)Endpoint Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
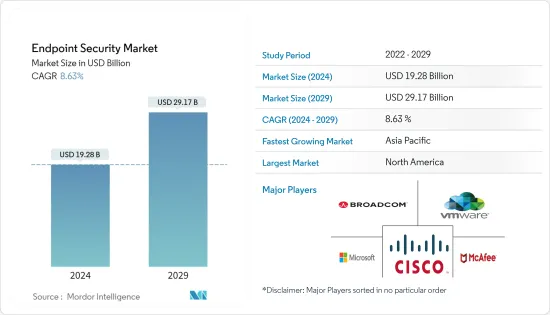
2024年端點安全市場規模預估為192.8億美元,預估至2029年將達291.7億美元,在預測期間(2024-2029年)成長8.63%,年複合成長率成長。
端點安全性保護最終用戶裝置(例如桌上型電腦、筆記型電腦和行動裝置)的端點或網路基地台免受惡意行為和宣傳活動的影響。端點安全技術可防止網路威脅到達網路或雲端中的端點。
隨著人口的成長和工業流程的數位化,個人電腦、筆記型電腦、智慧型手機、平板電腦和 POS 終端的數量急劇增加。隨著智慧型設備數量的增加,世界各地網路中的端點數量也在增加。隨著端點設備數量的增加,安全性變得必要。
許多行業的資料外洩事件不斷增加,數以百萬計的客戶資料記錄暴露給駭客,給一些受影響的公司和世界各地的終端用戶造成了數百萬美元的損失,端點安全解決方案正引起越來越多的關注。
隨著組織擴大採用 BYOD 趨勢,不同筆記型電腦、桌上型電腦和智慧型手機的湧入不斷增加,使不同的端點容易受到攻擊。僅靠安全措施不足以阻止他們。預計全球行動裝置採用率的大幅增加將在預測期內創造大量機會。根據思科的年度網際網路報告,到明年將有約 293 億台連網設備。隨著 5G 及其他技術的廣泛採用,智慧製造和智慧工業預計將成長。
端點安全市場已經飽和且商品化。隨著許多公司評估其供應商關係並尋求投資高效、強大的端點安全解決方案,市場正在顯著的新成長。
在 COVID-19 爆發期間,組織預計將透過促進職場的社交距離並允許在家辦公室進行遠端工作來採用端點安全解決方案。這促進了雲端基礎設施和服務的快速採用,導致市場領先設備的數量快速增加。
端點安全市場趨勢
預計製造業最終用戶細分市場將在預測期內大幅成長
- 工業物聯網 (IIoT) 和工業 4.0 正在增強生產流程,更好地控制庫存管理,並實現更高程度的自動化,但它們也為製造商在資料外洩方面帶來了新的漏洞。我做到了。這可能會導致資料遺失或遺失。洩漏。
- 製造商還在其系統上儲存了大量專門的敏感資料,包括正在進行的計劃、公司不希望披露的未來產品的設計,以及包含可能被駭客存取的敏感資訊的敏感財務資料。例如,電腦輔助設計 (CAD) 包含敏感訊息,可能會被駭客攻擊而生產仿冒品,或被感染或被木馬化以使攻擊者能夠存取關鍵系統。這是有可能的。
- 此外,製造業最近涉及資料外洩的攻擊有所增加。去年 5 月,總部位於東京的電動工具以及農業和工業機械製造商 Yamabiko 被添加到 Babuku Group 的 Babukransomware 使用的資料外洩網站中。此資料外洩包括有關員工的個人識別資訊 (PII)、財務資料、產品原理圖等。該組織聲稱總合持有0.5 TB 的資料。
- 此外,5G 連接的物聯網感測器的普及代表著製造商的潛在攻擊面正在迅速擴大。因為5G的出現將允許機器連接並傳輸即時資料。此類變更可能迫使端點安全供應商在未來部署創新產品。
預計北美將佔據最大的市場佔有率
- 北美是世界各地所有主要組織的主要樞紐。零售業的擴張和物聯網的成長正在推動該地區對智慧設備和行動裝置的需求。影響端點安全市場的攻擊風險多元:個人、企業和政府。因此,資料保護是該地區的首要任務。
- 此外,北美地區(尤其是美國)的網路攻擊正在迅速增加,並達到歷史最高水平,這主要是由於該地區連網設備數量的快速增加。
- 根據身分盜竊資源中心 (ITRC) 的數據,過去幾年,美國的平均違規數量略有增加。美國面臨的資料外洩事件從2017年的1,506起增加到去年的1,826起。
- 醫療資料的電子記錄正在迅速進步,該地區的醫療保健行業發生了許多資料外洩事件。因此,電子健康記錄和醫療記錄不斷增加,從而產生了對端點安全解決方案的需求。根據 HIPAA 的數據,醫療保健產業去年記錄了超過 686 起資料外洩事件,其中超過 4,499 萬筆記錄被洩露或被盜。
- 根據IBM今年發布的資料外洩成本報告統計,加拿大在資料外洩平均成本最高的國家中排名第三。去年該國資料外洩的平均損失為 540 萬美元,高於前年的 450 萬美元。
- 據加拿大網路安全中心稱,去年上半年全球勒索軟體攻擊增加了151%。網路中心報告了 235 起針對加拿大受害者的勒索軟體事件。此外,加拿大詐騙預防中心 (CAFC) 估計,去年加拿大人因詐騙損失了 1.7 億美元。
端點安全產業概述
端點安全市場由多個供應商根據各種規模進行細分,例如小型、區域性和大型跨國公司。由於市場競爭激烈,所有公司都專注於創造明確的價值和獨特的提案,以使其產品和服務與其他公司區分開來。老字型大小企業正在尋求收購規模較小的供應商以增強其產品組合。
- 2022年3月,Google宣布計畫以54億美元收購網路安全公司Mandiant。該協議代表了領先的雲端供應商對保護企業免受日益成長的威脅的廣泛承諾。
其他福利
- Excel 格式的市場預測 (ME) 表
- 3 個月分析師支持
目錄
第1章簡介
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章市場洞察
- 市場概況
- 產業吸引力-波特五力分析
- 供應商的議價能力
- 消費者議價能力
- 新進入者的威脅
- 替代品的威脅
- 競爭公司之間的敵意強度
- 評估 COVID-19 對產業的影響
第5章市場動態
- 市場促進因素
- 智慧型設備的成長
- 資料外洩增加
- 市場限制因素
- 對網路攻擊缺乏認知
第6章市場區隔
- 按最終用戶
- 消費者
- 工作
- BFSI
- 政府
- 製造業
- 衛生保健
- 能源和電力
- 零售
- 其他業務
- 按地區
- 北美洲
- 歐洲
- 亞太地區
- 拉丁美洲
- 中東和非洲
第7章 競爭形勢
- 公司簡介
- VMware Inc.
- Bitdefender LLC
- Avast Software SRO
- Fortinet Inc.
- ESET LLC
- Panda Security SL
- Kaspersky Lab Inc.
- Microsoft Corporation
- Sophos Group PLC
- Cisco Systems Inc.
- SentinelOne Inc.
- FireEye Inc.
- RSA Security LLC
- Palo Alto Networks Inc.
- Broadcom Inc.(Symantec Corporation)
- Trend Micro Inc.
- CrowdStrike Holdings Inc.
- McAfee LLC
- Blackberry Cylance
第8章投資分析
第9章市場機會與未來趨勢
The Endpoint Security Market size is estimated at USD 19.28 billion in 2024, and is expected to reach USD 29.17 billion by 2029, growing at a CAGR of 8.63% during the forecast period (2024-2029).

Endpoint security protects the endpoints or access points of end-user devices such as desktops, laptops, and mobile devices against malicious acts and campaigns. Endpoint security technologies prevent cyber threats from reaching endpoints on a network or in the cloud.
The number of PCs, laptops, smartphones, tablets, and point-of-sale terminals is increasing dramatically as the population grows and industrial processes become more digital. As the number of smart devices grows, so will the number of endpoints in networks worldwide. As a result of the increased number of endpoint devices, security is required.
The growing number of data breaches across many sectors has exposed millions of customer data records to hackers and resulted in the loss of millions of dollars for several impacted firms, increasing the emphasis on endpoint security solutions among various end users globally.
The increasing adoption of BYOD trends in organizations has increased the influx of different laptops, desktops, and smartphones, which has created different endpoints vulnerable to attacks. Security measures on their own are not enough to stop them. The massive growth in the adoption of mobile devices across the world is expected to create significant opportunities during the forecast period. According to the Cisco Annual Internet Report, there will be approximately 29.3 billion networked devices by next year. Smart manufacturing and the smart industry are expected to grow with the increased adoption of 5G and beyond.
The endpoint security market is saturated and commoditized. There is considerable renewed growth in the market as many companies are evaluating their vendor relationships and trying to invest in efficient and higher-functioning endpoint security solutions.
During the COVID-19 outbreak, organizations were expected to adopt endpoint security solutions by facilitating social distancing at work and allowing remote work-from-home offices. This has contributed to the rapid adoption of cloud infrastructure and services, leading to a rapid increase in the number of devices driving the market.
Endpoint Security Market Trends
Manufacturing End User Segment is Expected to Grow Significantly Over the Forecast Period
- While the Industrial Internet of Things (IIoT) and Industry 4.0 enhance production processes, provide more control over inventory management, and offer better automation, they have also created a new layer of vulnerabilities for manufacturers about data breaches, which could lead to data loss or leakage.
- Manufacturers also store a vast range of specialized and classified data on their systems, such as ongoing projects, designs for future products that companies may not like to expose, and confidential financial data that contains critical and confidential information that hackers can access. For instance, computer-aided design (CAD) contains secretive information that can be hacked to produce counterfeit goods or even infected or trojanized to enable attackers to access critical systems.
- In addition, the manufacturing sector has experienced an increase in attacks involving data breaches in recent times. In May last year, Yamabiko, a Tokyo-headquartered power tool and agricultural and industrial machinery manufacturer, was added to the data leak site used by the Babukgroup's Babukransomware. This data leak includes personally identifiable information (PII) on employees, financial data, product schematics, and many more. The group claimed to have a total of 0.5 TB of data.
- Further, the proliferation of 5G-connected IoT sensors indicates a radical expansion of the potential attack surface for manufacturers. This is because the advent of 5G will enable the connection of machinery and a stream of real-time data. Such transformations may compel endpoint security vendors to roll out innovative offerings in the future.
North America is Expected to Hold the Largest Market Share
- North America is a primary hub for all major organizations across the world. The expansion of the retail industry and the growth of IoT drive the demand for smart devices and mobiles in the region. The risks of attacks that can impact the endpoint security market vary from individuals and corporates to governments. Thus, protecting data has become a priority in the region.
- Moreover, cyberattacks in the North American region, especially in the United States, are rising rapidly and have reached an all-time high, primarily owing to the rapidly growing number of connected devices in the region.
- According to the Identity Theft Resource Center (ITRC), the average number of breaches in the United States has increased marginally over the past few years. The number of data breaches faced by the United States increased from 1,506 breaches in 2017 to 1,826 violations in the last year.
- The healthcare industry in the region is also witnessing many data breaches as health-related data is moving rapidly toward electronic records. This has resulted in an increase in electronic health and medical records, which require endpoint security solutions. According to HIPAA, the healthcare sector recorded more than 686 data breaches last year, including the exposure or theft of more than 44.99 million records.
- According to statistics in the Cost of Data Breach Report published by IBM this year, Canada ranked third in terms of the highest average data breach cost. The country's average cost of data breaches stood at USD 5.40 million last year, up from USD 4.50 million the year before.
- According to the Canadian Center for Cyber Security, ransomware attacks increased by 151% globally in the first half of last year. The Cyber Center reported 235 ransomware incidents against victims in Canada. Further, the Canadian Anti-Fraud Centre (CAFC) estimated that Canadians lost USD 170 million due to fraud in the previous year.
Endpoint Security Industry Overview
The endpoint security market is fragmented by several vendors based on all scales, i.e., small-scale, regional, and large multi-national scales. Due to intense rivalry in the market, all players are focusing on creating clear value and unique propositions to differentiate their products and services from others. Well-established companies are trying to acquire small-scale vendors to enhance their portfolios.
- In March 2022, Google announced its plan to acquire cybersecurity firm Mandiant for USD 5.4 billion. The deal represents a broad effort by leading cloud providers to help enterprises protect themselves from growing threats.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Consumers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitutes
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Assessment of Impact of COVID-19 on the Industry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Growth in Smart Devices
- 5.1.2 Increasing Number of Data Breaches
- 5.2 Market Restraints
- 5.2.1 Lack of Awareness about Cyberattacks
6 MARKET SEGMENTATION
- 6.1 By End User
- 6.1.1 Consumer
- 6.1.2 Business
- 6.1.2.1 BFSI
- 6.1.2.2 Government
- 6.1.2.3 Manufacturing
- 6.1.2.4 Healthcare
- 6.1.2.5 Energy and Power
- 6.1.2.6 Retail
- 6.1.2.7 Other Businesses
- 6.2 By Geography
- 6.2.1 North America
- 6.2.2 Europe
- 6.2.3 Asia-Pacific
- 6.2.4 Latin America
- 6.2.5 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 VMware Inc.
- 7.1.2 Bitdefender LLC
- 7.1.3 Avast Software SRO
- 7.1.4 Fortinet Inc.
- 7.1.5 ESET LLC
- 7.1.6 Panda Security SL
- 7.1.7 Kaspersky Lab Inc.
- 7.1.8 Microsoft Corporation
- 7.1.9 Sophos Group PLC
- 7.1.10 Cisco Systems Inc.
- 7.1.11 SentinelOne Inc.
- 7.1.12 FireEye Inc.
- 7.1.13 RSA Security LLC
- 7.1.14 Palo Alto Networks Inc.
- 7.1.15 Broadcom Inc. (Symantec Corporation)
- 7.1.16 Trend Micro Inc.
- 7.1.17 CrowdStrike Holdings Inc.
- 7.1.18 McAfee LLC
- 7.1.19 Blackberry Cylance













