 |
市場調查報告書
商品編碼
1440171
資訊安全諮詢:市場佔有率分析、產業趨勢與統計、成長預測(2024-2029)Information Security Consulting - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
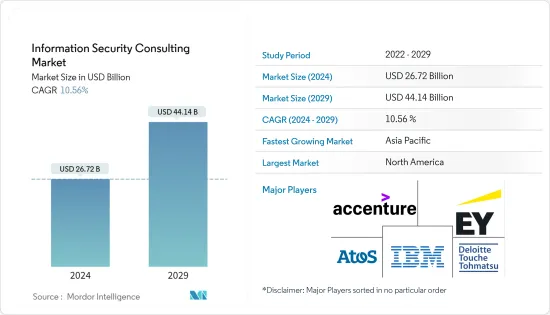
資訊安全諮詢市場規模預計到2024年為267.2億美元,預計到2029年將達到441.4億美元,在預測期內(2024-2029年)成長10.56%,年複合成長率成長。
由於併購和第三方應用程式部署而導致的網路複雜性不斷增加、物聯網設備安全威脅不斷增加、BYOD 趨勢不斷成長等是推動市場成長的一些關鍵因素。
主要亮點
- 隨著物聯網等新技術的引入,對數位環境的大力推動增加了對第三方服務供應商保護寶貴資產免受網路攻擊的需求。據思科稱,到 2023 年,連網型設備預計將達到 293 億台。該公司還預計,到 2023 年,物聯網將普及所有機器對機器技術的 50%,並普及約 53 億人。
- 各個最終用戶產業的組織正在將物聯網設備作為其數位轉型策略的優先事項。根據微軟的物聯網訊號第 2 版調查,3,000 名業務和技術決策者和開發人員中,90% 的人表示物聯網對其公司的成功至關重要。
- 此外,美國、英國、德國、法國、中國和日本各產業約 64% 的決策者計劃在未來實施更多物聯網計劃。 Accenture PLC 等 IT 顧問公司提供保全服務來減輕對物聯網硬體的攻擊。
- 根據 Verizon 的 2022 年資料外洩報告,該報告基於 80 多個組織的資料,與前一年相比,全球大多數最終用戶領域的外洩事件都在增加。 Verizon 分析了 23,896 起現實世界安全事件,其中 5,212 起被確認受到損害。在 Verizon 分析的 4,250 起資料外洩事件中,約有 50% 是由憑證造成的,超過 15% 是由網路釣魚造成的,超過 15% 是由網路釣魚造成的,其餘則是由殭屍網路造成的。
- 在許多情況下,來自不同最終使用者部門的組織會受到複雜網路攻擊的影響。 2022年4月,哥斯大黎加政府財政部遭駭客攻陷。這些駭客控制了該部門的電腦系統,並要求政府支付 1000 萬美元才能恢復存取權限。當政府拒絕後,駭客對大約 30 個政府機構進行了網路攻擊。
資訊安全諮詢市場趨勢
BFSI 預計將出現顯著成長
- BFSI 產業面臨著與研究中討論的其他最終用戶不同的三個挑戰。這些挑戰是發展資訊安全諮詢服務的主要驅動力。由於資料的敏感性,該行業比任何其他行業都面臨更多的網路犯罪分子攻擊。
- 該行業經常面臨高級且持續的攻擊,包括惡意軟體、勒索軟體、社交工程攻擊、網路釣魚攻擊、無文件惡意軟體、 套件和注入攻擊。Accenture估計,金融服務機構每年的平均損失為 1,800 萬美元。
- 銀行業面臨的最常見的惡意軟體攻擊包括無簽名和無文件惡意軟體。這些程式的行為與其他惡意程式不同,而是利用底層進程來隱藏其活動。由於攻擊頻繁發生,因此必須採取足夠的安全措施來降低與資料外洩和網路攻擊相關的風險,包括資料遺失、無法操作、業務損失以及復原成本和時間。
- 金融公司面臨更高的風險合規要求。未能保護其財務資訊的公司將面臨罰款、法律費用和業務損失。零時差攻擊和勒索軟體均呈上升趨勢。勒索軟體可能會對財務工作流程產生重大負面影響,導致代價高昂的停機並損害企業聲譽。所有上述因素都促進了全球資訊安全諮詢市場的成長。
亞太地區將經歷顯著成長
- 亞洲 BFSI 產業數位化的不斷發展預計將在預測期內增加對資訊安全諮詢服務的需求。為了應對這一突然而重大的變化,銀行期待實施網路安全、端點設備、應用程式以及資料庫解決方案和服務。
- 亞太地區佔據該細分市場的大部分佔有率。根據印度資料安全委員會 (DSCI) 的數據,BFSI 是印度網路安全支出市場佔有率最大的三大產業之一。這是由於監管機構、資料本地化、公用事業收費支付、電子商務和線上保險市場的標準收緊。此類措施預計將增加該國端點安全解決方案的採用。
- 該地區網路攻擊的增加迫使參與者加強防禦能力。國際供應商需要印度等國家更多的本地資源,這使得實施和技術支援變得困難。因此,區域組織也在調整Start-Ups提供的服務,與老牌公司相比,新創公司提供全面的支援和彈性價格設定。這有望為資訊安全領域Start-Ups的成長創建一個生態系統。
- 同時,公共雲端運算的採用正在增加,越來越多的公司將其業務系統重新分配到雲端平台。與資料安全、租戶隔離、存取控制等相關的問題預計將推動資訊安全諮詢市場的發展。
資訊安全諮詢產業概況
資訊安全諮詢市場有些分散。在市場上的所有參與者中,占主導地位的參與者佔據了大部分市場佔有率,這增加了競爭公司之間的敵意。老字型大小企業正在尋求收購規模較小的供應商以增強其產品組合。
- 2022 年 3 月 - 沃達豐和埃森哲合作,為德國中小型企業提供資安管理服務。該服務可協助中小型企業增強抵禦網路威脅的能力,並為需要更多能力、時間和資源以跟上這個快速發展的領域的專業知識的組織提供一流的網路安全人才和行業支援。
- 2022 年 1 月 - 惠普企業宣布與阿拉伯聯合大公國網路安全委員會簽署合作備忘錄,以加強學校的網路技能培訓,並為阿拉伯聯合大公國青年在科技產業的職業生涯做好準備。
其他福利
- Excel 格式的市場預測 (ME) 表
- 3 個月分析師支持
目錄
第1章 簡介
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章市場動態
- 市場概況
- 產業價值鏈分析
- 產業吸引力-波特五力分析
- 供應商的議價能力
- 消費者議價能力
- 新進入者的威脅
- 競爭公司之間的敵意強度
- 替代品的威脅
- COVID-19 對市場的影響
第5章市場動態
- 市場促進因素
- 增加網路複雜性
- 提高攻擊複雜性
- 市場限制因素
- 實施資訊安全諮詢服務的預算限制
第6章市場區隔
- 按類型
- 安全性和合規性
- 防火牆管理
- 電子郵件和雲端安全
- 其他IT諮詢
- 依部署方式
- 本地
- 雲
- 按組織規模
- 中小企業
- 主要企業
- 按最終用戶產業
- 銀行、金融服務和保險
- 資訊科技和電信
- 航太和國防
- 政府
- 衛生保健
- 按行業分類的其他最終用戶
- 地區
- 北美洲
- 歐洲
- 亞太地區
- 拉丁美洲
- 中東和非洲
第7章 競爭形勢
- 公司簡介
- Ernst &Young Global Limited
- IBM Corporation
- Accenture PLC
- Atos SE
- Deloitte Touche Tohmatsu Limited(DTTL)
- KPMG International Cooperative
- Pricewaterhousecoopers
- Bae Systems PLC
- Hewlett Packard Enterprise
- Wipro Limited
- Optiv Security Inc.
- Dell SecureWorks Inc.
第8章投資分析
第9章 市場的未來
The Information Security Consulting Market size is estimated at USD 26.72 billion in 2024, and is expected to reach USD 44.14 billion by 2029, growing at a CAGR of 10.56% during the forecast period (2024-2029).

Rising network complexities due to mergers and acquisitions and third-party application deployment, increasing threats to the security of IoT devices, and the growing trend of BYOD are some of the major factors driving the growth of the market.
Key Highlights
- The significant push toward a digital environment with the adoption of new technologies, such as IoT, is developing a need for third-party service providers to protect valuable assets from cyber-attacks. According to CISCO, connected devices are expected to reach 29.3 billion by 2023. The company also anticipates that IoT is expected to spread across 50% of all machine-to-machine technology that will reach about 5.3 billion people by 2023.
- Organizations across different end-user industries are making IoT devices a priority of their digital transformation strategy. According to Microsoft's IoT signal edition 2 survey, 90% of the 3,000 business and technical decision-makers and developers suggested IoT is critical to their company's success.
- In addition, about 64% of the decision-makers across a range of industries in the United States, the United Kingdom, Germany, France, China, and Japan are planning to implement more IoT projects in the future. IT consulting companies, such as Accenture PLC and others, offer security services to mitigate attacks on IoT hardware.
- Compared to the previous year, there has been a growth in breaches across most end-user verticals, according to Verizon's 2022 Data Breach Report globally, based on data from more than 80 organizations. Verizon analyzed 23,896 real-world security incidents, of which 5,212 were confirmed breaches. Out of 4,250 data breaches Verizon analyzed, approximately 50% were enabled through credentials, 15+% were enabled through phishing, 15+% were enabled through phishing, and the remaining were enabled through botnets.
- There have been several cases where organizations across different end-user verticals have been affected by sophisticated cyber attacks. In April 2022, the finance ministry of the Costa Rican government was overtaken by hackers. These hackers took control of the ministry's computer systems and demanded USD 10 million to return access back to the government. When the government refused, the hackers carried out cyber attacks against around 30 government agencies.
Information Security Consultant Market Trends
BFSI is Expected to Witness Significant Growth
- The BFSI industry faces three challenges distinct from any other end-users discussed in the study. These challenges are the major driving forces for deploying information security consulting services. The industry faces more attacks from cybercriminals than any other sector due to high data sensitivity.
- The industry frequently faces sophisticated and persistent attacks, including malware, ransomware, social engineering and phishing attacks, fileless malware, rootkits, and injection attacks. Accenture estimates an average loss of USD 18 million annually at financial services institutions.
- Some of the most common malware attacks the banking industry face include signature-less and fileless malware, which do not behave like other malicious programs but exploit fundamental processes to hide their activities. Due to frequent attacks, it becomes critical to have adequate security to mitigate the risks related to a data breach or any cyber-attack, such as loss of data, inoperability, lost business, and recovery cost and time.
- Financial enterprises face considerably higher stakes compliance requirements. The failure of financial information security causes the business to face fines, legal fees, and lost business. Both zero-day attacks and ransomware are on the rise. Ransomware can negatively affect financial workflows significantly, inflicting costly downtime and damaging business reputations. All the above factors contribute to the growth of the global information security consulting market.
Asia-Pacific to Witness Significant Growth
- The rise in digitization across Asia in the BFSI sector is expected to drive the demand for information security consulting services over the forecast period. To cope with this sudden colossal change, banks are looking forward to adopting solutions and services for the network's security, endpoint devices, applications, and databases.
- Asia-Pacific occupies the majority of the share in this segment. According to the Data Security Council of India (DSCI), BFSI is one of India's top three sectors with the largest market share in cybersecurity expenditure. This is due to tightened norms from regulators, data localization, utility payments, e-commerce, and online insurance marketplaces. Such initiatives are expected to increase the adoption of endpoint security solutions in the country.
- The increasing cyber-attacks in the region have propelled the players to strengthen their defensive capabilities. International vendors need more regional resources in countries like India, which causes difficulty in implementation and technical support. As a result, regional organizations are also adapting services offered by startups that provide complete support and flexible pricing compared to established players. This is expected to develop an ecosystem for the growth of startups in the information security arena.
- On the other hand, the increasing adoption of public cloud computing leads to more enterprises re-allocating their business systems to cloud platforms. Issues concerning data security, tenant isolation, access control, etc., are expected to propel the market for information security consulting.
Information Security Consultant Industry Overview
The information security consulting market is moderately fragmented. Among all the players present in the market, leading players hold most of the market share, and therefore, the competitive rivalry is high. Well-established companies are trying to acquire small-scale vendors to enhance their portfolios.
- March 2022 - Vodafone and Accenture partnered to provide managed security services to small to medium-sized enterprises in Germany. The services will help SMEs be more resilient to cyber threats, providing leading cybersecurity talent and industry expertise to organizations that need more capacity, time, and resources to keep up with this rapidly evolving space.
- Jan 2022 - Hewlett Packard Enterprise announced that the company had signed a memorandum of understanding with the UAE Cyber Security Council to enhance cyber skills training in schools and prepare Emirati youth for careers in the technology industry.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Suppliers
- 4.3.2 Bargaining Power of Consumers
- 4.3.3 Threat of New Entrants
- 4.3.4 Intensity of Competitive Rivalry
- 4.3.5 Threat of Substitutes
- 4.4 Impact of COVID-19 on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Rising Network Complexities
- 5.1.2 Increased Sophistication in Attacking
- 5.2 Market Restraints
- 5.2.1 Budget Constraints in the Adoption of Information Security Consulting Services
6 MARKET SEGMENTATION
- 6.1 By Type**
- 6.1.1 Security and Compliance
- 6.1.2 Firewall Management
- 6.1.3 Email and Cloud Security
- 6.1.4 Other IT Consulting
- 6.2 By Deployment Mode
- 6.2.1 On Premise
- 6.2.2 Cloud
- 6.3 By Organization Size
- 6.3.1 Small and Medium Enterprises
- 6.3.2 Large Enterprises
- 6.4 By End user Vertical
- 6.4.1 Banking, Financial Services, and Insurance
- 6.4.2 IT and Telecom
- 6.4.3 Aerospace and Defense
- 6.4.4 Government
- 6.4.5 Healthcare
- 6.4.6 Other End-user Vertical
- 6.5 Geography
- 6.5.1 North America
- 6.5.2 Europe
- 6.5.3 Asia-Pacific
- 6.5.4 Latin America
- 6.5.5 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Ernst & Young Global Limited
- 7.1.2 IBM Corporation
- 7.1.3 Accenture PLC
- 7.1.4 Atos SE
- 7.1.5 Deloitte Touche Tohmatsu Limited (DTTL)
- 7.1.6 KPMG International Cooperative
- 7.1.7 Pricewaterhousecoopers
- 7.1.8 Bae Systems PLC
- 7.1.9 Hewlett Packard Enterprise
- 7.1.10 Wipro Limited
- 7.1.11 Optiv Security Inc.
- 7.1.12 Dell SecureWorks Inc.








