 |
市場調查報告書
商品編碼
1406186
零信任安全:市場佔有率分析、產業趨勢/統計、2024-2029 年成長預測Zero Trust Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts 2024 - 2029 |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
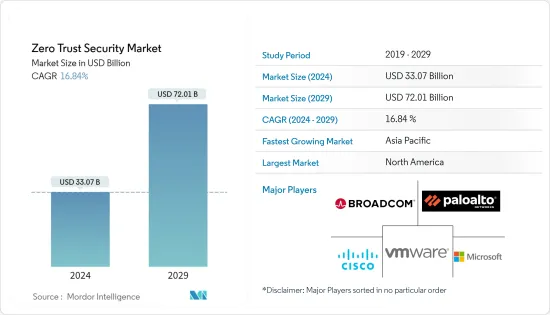
預計到 2024 年,零信任安全市場規模將達到 330.7 億美元,預計到 2029 年將達到 720.1 億美元,在預測期內(2024-2029 年)複合年成長率為 16.84%。
主要亮點
- 近年來,一種稱為「零信任安全」的不斷發展的網路安全策略獲得了廣泛的關注和接受。零信任方法的前提是「從不信任,始終檢驗」這句格言,並假設威脅可能來自內部和外部來源。隨著企業越來越意識到需要在威脅環境更加複雜和動態的環境中保護其網路、應用程式和資料,對零信任安全解決方案的需求也在不斷成長。
- 隨著網路威脅的數量和複雜性不斷增加,包括資料外洩、勒索軟體攻擊和內部威脅,組織越來越注重實施零信任等強大的安全措施。 COVID-19 的爆發加速了遠距工作的普及,增加了攻擊面。零信任是保護分散式遠距勞動力的關鍵策略。
- 向雲端運算的轉變迫使組織重新考慮他們的安全狀況。零信任支援安全存取雲端基礎的應用程式和資料,非常適合雲端優先計劃。組織必須開發強大的資料保護機制,以遵守 GDPR 和 CCPA 等嚴格的資料隱私法,而零信任可以實現合規性。企業擴大在各個領域利用零信任框架作為基本安全策略。傳統的基於邊界的範式正在被放棄。大型科技公司正在收購零信任安全業務,以改善其安全服務。
- 組織正在採用 DevOps 策略並將零信任概念涵蓋其 DevOps 管道中,以確保安全性成為開發過程的一部分。專注於安全遠端存取的零信任網路存取 (ZTNA) 領域出現了顯著成長。考慮到遠端工作的普及以及安全存取公司資源的需要,這一點尤其重要。徹底實施零信任策略具有挑戰性且耗時。身分和存取管理、網路安全和分析是組織需要規劃和整合的一些要素。
- 零信任對於安全至關重要,但企業必須在嚴格的安全措施與流暢有效的使用者體驗之間取得平衡。要找到理想的平衡是很困難的。許多公司繼續使用過時的架構和系統,這使得實施零信任原則變得困難。從這些系統遷移需要時間和精力。使用者資訊外洩和內部威脅仍然是主要的安全問題。網路釣魚和其他社會工程攻擊仍然是常見的攻擊方法。
- 不斷變化的威脅情勢和對徹底安全措施的需求正在導致全球零信任安全市場的顯著擴張。然而,企業面臨重大挑戰,因為他們使用的是過時的作業系統、基礎設施和應用程式。抵制這些組件採用零信任概念應該會提高更廣泛的市場採用率。
- COVID-19大流行產生了積極影響,提供了非接觸式付款模式,包括線上和實體交易。這包括廣泛的數位基礎設施,並使金融系統面臨網路安全漏洞,從而對零信任安全等強大的安全模型產生了巨大的需求。例如,根據印度儲備銀行 (RBI) 的數據,2022 會計年度印度各地進行了約 710 億筆數付款。這比前三年有顯著成長。
零信任安全市場趨勢
BFSI 部門成為最大的最終用戶
- 國際貨幣基金組織 (IMF) 表示,銀行、金融服務和保險 (BFSI) 領域內的金融和技術互連促進了網路攻擊的迅速擴散,導致整個金融生態系統的廣泛破壞和敏感資訊損失。它正在造成損失。網路安全對金融穩定構成重大威脅,尤其是在新興經濟體。
- 國際貨幣基金組織最近對 51 個國家進行的一項調查發現,新興市場的大多數金融監督仍需要引入網路安全法規或建立資源來執行這些法規。調查發現,56%的央行機構需要國家網路戰略,42%的機構缺乏專門的網路安全或風險管理法規,68%的機構缺乏專門的風險部門;特別強調的是,64%的機構不需要測試和演練網路安全措施。
- 根據 IBM 的《2022 年資料外洩成本》報告,2022 年資料外洩事件激增。同年平均資料外洩成本達 435 萬美元,較 2021 年成長 2.6%。該報告還發現,包括銀行在內的 83% 的組織將在 2022 年報告至少一起資料外洩事件。
- 隨著銀行和金融機構將其平台遷移到雲端,雲端的採用在全球銀行和金融領域迅速普及。隨著混合雲的興起,企業擴大評估跨多個雲端供應商分發服務的好處。多重雲端方法和網際網路服務的激增正在推動更多消費者使用網際網路和行動應用程式進行交易。
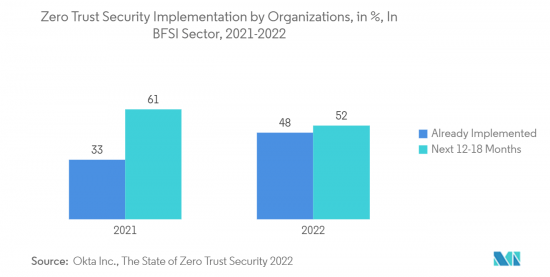
- BFSI 產業是全球經濟最重要的部門之一,由大公司主導。幾家領先的零售、商業和投資銀行公司正在採用零信任網路安全方法,以確保現代企業的普遍存在並應對不斷發展的商業模式的挑戰。根據《2022 年零安全狀況》,BFSI 領域組織對零信任安全的採用預計將大幅增加。
預計北美將佔據較大市場佔有率
- 美國是一個已開發經濟體,強烈傾向於採用和擁抱先進技術、開拓網路自動化和激增雲端基礎的服務,為零信任安全市場做出貢獻。此外,最終用戶產業數位化程度的提高以及Cisco、IBM 公司、供應商 Palo Alto Networks 和 Akamai Technologies 的存在也為市場成長做出了貢獻。
- 網路攻擊者的典型目標是端點設備、雲端基礎的應用程式、網路和其他IT基礎設施元件。此類攻擊背後的主要動機是竊取重要資訊。此類攻擊可能會導致業務中斷、財務損失、知識產權被盜以及關鍵和敏感客戶資訊的遺失。美國聯邦政府正朝著「零信任」邁出重大步伐。 2023 年 1 月,管理與預算辦公室發布了一份備忘錄,強制聯邦政府實施零信任架構(ZTA) 策略,指示各機構在 2024 財政年度結束前實現具體的網路安全措施和目標。這項舉措加強了政府對日益複雜和持續的威脅宣傳活動的防禦能力。
- 此外,新技術的快速採用以及該國對安全的日益重視正在推動對安全即服務(SaaS) 的需求。持有敏感資訊資料庫的行業(例如銀行、醫療保健和政府機構)由於包含大量資訊,因此很容易成為駭客的目標。信用卡資料和個人的社會安全號碼是駭客攻擊的目標資訊。為了保護此類關鍵資料,需要強大的雲端入侵防護和安全解決方案以及適當的網路安全解決方案。為此,分析認為未來幾年對零信任解決方案的需求將會增加。
- 2021 年,美國針對組織的勒索軟體和網路釣魚攻擊增加,手動程度越來越低,自動化程度更高。根據 Emsisoft 2023 年 1 月發布的年終報告,儘管美國政府努力阻止這項威脅,但學校在 2022 年遭受的網路攻擊數量幾乎與 2021 年相同。國內市場供應商積極開展合作活動,為客戶提供高效、強大的安全存取服務邊際產品,以安全地加速其數位轉型計劃。例如,2023 年 7 月,安全存取服務邊際(SASE) 供應商 Netscope 宣布與 Wipro Limited 開展新合作,為 Wipro 提供託管零信任網路存取(ZTNA) 和強大的雲端原生託管安全交付存取服務邊際(SASE)服務。廣泛的全球企業客戶組合。
- 總體而言,據分析,北美零信任市場在未來幾年將顯著成長,這主要是由於最終用戶行業雲端遷移的增加以及雲端服務和零信任市場中供應商的增加。此外,不斷推出新的和增強的解決方案以及供應商之間活性化的合作夥伴關係活動將推動未來幾年的市場成長。此外,該地區的其他行業領域,如製造業、能源和公共產業,已轉向並開始了解數位化業務方式,因此存在巨大的成長潛力。
零信任安全產業概述
零信任安全市場的特點是競爭形勢激烈,思科系統公司、帕洛阿爾托網路公司、VMware 公司、博通公司和微軟公司等全球和區域參與者都在爭奪市場佔有率。進入壁壘很高,但一些新參與企業已成功在該行業站穩腳跟。
該市場的特點是產品差異化程度較高、產品普及不斷提高、競爭激烈。解決方案通常捆綁在一起,以提供作為整體服務或產品一部分的整合服務。
許多用戶選擇年度合約來降低成本,而企業也擴大尋求提供更快安全更新的服務。這增加了對雲端基礎的服務的需求,這些服務允許即時更新,並且受到酒店業的青睞。
其他福利
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
目錄
第1章簡介
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章市場洞察
- 市場概況
- 產業吸引力-波特五力分析
- 供應商的議價能力
- 買方議價能力
- 新進入者的威脅
- 替代品的威脅
- 競爭公司之間的敵對關係
- COVID-19 的影響
- 產業價值鏈分析
- 技術簡介
- 零信任網路
- 零信任設備
- 零信任資料
- 零信任身份
- 零信任應用程式(可見性和分析)
第5章市場動態
- 市場促進因素
- 資料外洩增加
- 您組織的安全範圍不僅限於職場
- 市場抑制因素
- 遺留應用程式、基礎架構和作業系統使得採用零信任模型變得困難
第6章市場區隔
- 按發展
- 本地
- 雲
- 按組織規模
- 中小企業
- 主要企業
- 按最終用戶產業
- 資訊科技/通訊
- BFSI
- 製造業
- 衛生保健
- 能源/電力
- 零售業
- 政府機關
- 其他最終用戶產業
- 按地區
- 北美洲
- 歐洲
- 亞太地區
- 世界其他地區
第7章競爭形勢
- 公司簡介
- Cisco Systems Inc.
- Palo Alto Networks, Inc.
- Vmware, Inc.
- Broadcom Inc.(Symantec Corporation)
- Microsoft Corporation
- IBM Corporation
- Google LLC(Alphabet Inc.)
- Check Point Software Technologies Ltd
- BlackBerry Limited
- Akamai Technologies Inc.
- DELINEA(Centrify Corporation)
- Okta Inc.
- Fortinet, Inc.
- Sophos Ltd.
- Cyxtera Technologies Inc.
第8章投資分析
第9章市場的未來

The Zero Trust Security Market size is estimated at USD 33.07 billion in 2024, and is expected to reach USD 72.01 billion by 2029, growing at a CAGR of 16.84% during the forecast period (2024-2029).
Key Highlights
- A developing cybersecurity strategy called zero trust security has attracted a lot of attention and acceptance in recent years. The zero trust approach is predicated on the maxim 'never trust, always verify,' which makes assumptions that threats might originate from internal and external sources. The need for zero-trust security solutions has increased as enterprises increasingly acknowledge the need to secure their networks, apps, and data in an environment with a more complex and dynamic threat landscape.
- Organizations are concentrating more on implementing strong security measures like Zero Trust due to the increased number and sophistication of cyber threats, including data breaches, ransomware attacks, and insider threats. The popularity of remote work was accelerated by the COVID-19 pandemic, increasing the attack surface. Zero trust is a crucial strategy for protecting distributed and remote workforces.
- Organizations have had to review their security postures due to the move toward cloud computing. Zero trust facilities secure access to cloud-based apps and data, which fits well with cloud-first plans. Organizations must develop robust data protection mechanisms to comply with strict data privacy laws like GDPR and CCPA, making zero trust a compliance enabler. Businesses use the zero trust framework in various sectors more widely as a fundamental security strategy. The conventional perimeter-based paradigm is being abandoned. Big technology corporations are buying zero trust security businesses to improve security services.
- Organizations are incorporating zero trust concepts into their DevOps pipelines as they adopt DevOps strategies to ensure security is a part of the development process. A significant increase has been observed in the secure remote access-focused zero trust network access (ZTNA) sector. This is particularly pertinent given the prevalence of remote work and the requirement for safe access to company resources. A thorough zero trust strategy's implementation can be challenging and time-consuming. Identity and access management, network security, and analytics are a few components that organizations need to plan and integrate.
- Zero trust is crucial for security, but businesses must strike a balance between strict security measures and a smooth, effective user experience. Finding the ideal balance is difficult. Many businesses continue to use outdated architectures and systems that make it difficult to implement zero-trust principles. Migrating away from these systems can take time and effort. The compromise of user credentials and insider threats remain major security worries. Phishing and other social engineering assaults are still common attack methods.
- The constantly changing threat landscape and the demand for thorough security measures have led to a major increase in the global zero-trust security market. However, enterprises have a big problem because of outdated operating systems, infrastructure, and applications. The wider market adoption needs to be improved by the resistance of these antiquated components to adopt the zero trust concept.
- The COVID-19 pandemic had a positive impact, providing a contactless payment mode, including online and in-person transactions. This has included the digital infrastructure extensively, exposing the financial system to cybersecurity vulnerabilities, which created considerable demand for fool-proof security models like zero trust security. For instance, according to RBI, approximately 71 billion digital payments were made throughout India in fiscal year 2022. This was a significant increase over the preceding three years.
Zero Trust Security Market Trends
BFSI Sector to be the Largest End User
- The International Monetary Fund (IMF) reveals that financial and technological interconnections within the banking, financial services, and insurance (BFSI) sector facilitate the rapid spread of cyberattacks, causing widespread disruption and loss of critical information throughout the entire financial ecosystem. Cybersecurity is a significant threat to financial stability, especially among the developing economies.
- A recent IMF survey of 51 countries states that most financial supervisors in emerging markets still need to introduce cybersecurity regulations or build resources to enforce them. The survey highlights that 56% of the central bank authorities need a national cyber strategy, 42% lack a dedicated cybersecurity or risk-management regulation, 68% lack a specialized risk unit, and 64% do not mandate testing and exercising cyber security measures.
- According to IBM's 'Cost of a Data Breach 2022' report, 2022 witnessed a surge in data breaches. The average data breach cost reached USD 4.35 million in the same year, marking a 2.6% increment from 2021. The report also states that 83% of organizations, including banks, reported more than one data breach in 2022.
- Cloud deployments are gaining rapid popularity in the global banking and financial sector as banks and financial institutions migrate their platforms to the cloud. With the rise of hybrid cloud, businesses increasingly appreciate the advantages of diversifying their services across multiple cloud providers. A multi-cloud approach and rapid increase of internet services enable more and more consumers to use the internet and mobile applications for transactions.
- Large enterprises dominate the BFSI industry, one of the most important sectors of the global economy. Several large retail banking, commercial banking, and investment banking organizations are taking a zero-trust approach to cybersecurity to help secure the ubiquitous nature of modern enterprises and meet the challenges caused by evolving business models. As per The State of Zero Security 2022, the implementation of zero trust security by organizations in the BFSI sector is expected to increase significantly.

North America is Expected to Hold Significant Market Share
- The United States is a developed economy with a significant inclination towards implementing and accepting advanced technology, development in network automation, and the surge in cloud-based services, thereby contributing to the zero trust security market. Moreover, the growing digitization among end-user industries, coupled with the presence of prominent market vendors Cisco Systems, Inc., IBM Corporation, Vmware Inc., Palo Alto Networks, and Akamai Technologies, contribute to the market's growth.
- Cyber attackers with a typical target go after end-point devices, cloud-based applications, networks, and other IT infrastructure components. The primary motive behind such attacks is to steal critical information. These attacks can result in business disruptions, financial loss, intellectual property theft, and critical and sensitive customer information loss. The US federal government is making a big push toward zero trust. In January 2023, the Office of Management and Budget released a memorandum that mandates a federal zero trust architecture (ZTA) strategy, directing agencies to meet specific cyber security measures and objectives by the end of the fiscal year 2024. This initiative reinforces the government's defenses against increasingly sophisticated and persistent threat campaigns.
- Further, the rapid adoption of new technology in the country and growing focus on security is pushing the demand for security-as-a-service forward. Industries, such as banking, healthcare, and government organizations, which hold databases of sensitive information, are preferred targets for hackers owing to the huge amount of information contained. Credit card data and social security numbers of individuals are the targeted information attacked by the hackers. To safeguard such critical data, there is a need for robust cloud intrusion protection and security solutions, along with suitable network security solutions. This is analyzed to boost the demand for zero-trust solutions in the coming years.
- The United States marked the increase of ransomware and phishing attacks targeted at organizations that involved less manual effort and were highly automated in 2021. According to Emsisoft's year-end report published in January 2023, Schools sustained almost the same number of cyberattacks in 2022 as in 2021, despite the US government's efforts to thwart the threat. Market vendors in the country are indulging in partnership activities to provide customers with an efficient and robust secure access service edge offering to secure and accelerate their digital transformation projects. For instance, in July 2023, Netskope, a Secure Access Service Edge (SASE) provider, announced a new collaboration with Wipro Limited to deliver Managed Zero Trust Network Access (ZTNA) and robust cloud-native Managed Secure Access Service Edge (SASE) services to Wipro's extensive global enterprise client portfolio.
- Overall, the zero trust market in North America is analyzed to witness substantial growth in coming years, primarily governed by the increasing cloud migration in end-user industries, coupled with the growing presence of cloud service and Zero Trust market vendors. In addition, the continuous launch of new solutions with enhanced features and growing partnership activities among market vendors will drive the growth of the market in the coming years. Moreover, there is huge growth potential from other industry segments in the Region, such as manufacturing, energy, and utilities, as they have already migrated to digital-transformed methods of operations and are now beginning to get a better understanding.
Zero Trust Security Industry Overview
The zero trust security market features a competitive landscape with global and regional players such as Cisco Systems Inc., Palo Alto Networks Inc., Vmware Inc., Broadcom Inc., and Microsoft Corporation vying for market share. Despite significant barriers to entry, some new entrants have managed to gain a foothold in this space.
This market is characterized by a moderate to high degree of product differentiation, a growing level of product adoption, and intense competition. Typically, solutions are bundled together, creating a consolidated offering that appears integral to the overall service or product.
Many users opt for annual contracts to reduce costs, and there is a growing trend of companies seeking services that offer faster security updates. This has fueled a rising demand for cloud-based services, which enable real-time updates and are favored by service-based industries.
For instance, in July 2023, Microsoft Entra made significant strides in the Security Service Edge (SSE) arena, introducing two innovative products: Microsoft Entra Internet Access and Microsoft Entra Private Access. These cloud-based services are known for their agility, easy management, and cost-effectiveness when compared to traditional on-premises systems. They adhere to Zero Trust principles, verifying each user's identity and employing risk-based contextual information to grant access only to the necessary applications, resources, and destinations, ensuring optimal security without compromising productivity.
In June 2023, Cisco Systems expanded its security portfolio by unveiling a new Security Service Edge (SSE) solution called Cisco Secure Access. This solution facilitates an efficient hybrid work environment, simplifying access across different locations, devices, and applications. Cisco Secure Access offers frictionless access to all applications, fostering secure hybrid work settings. The solution streamlines security operations by consolidating multiple functions into a user-friendly solution that safeguards all traffic. This not only enhances efficiency and reduces costs but also adds flexibility to the IT environment.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHT
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Buyers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitutes
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Impact of COVID-19
- 4.4 Industry Value Chain Analysis
- 4.5 Technology Snapshot
- 4.5.1 Zero Trust Networks
- 4.5.2 Zero Trust Devices
- 4.5.3 Zero Trust Data
- 4.5.4 Zero Trust Identities
- 4.5.5 Zero Trust Applications (Visibility and Analytics)
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increasing Number of Data Breaches
- 5.1.2 Security Perimeter of an Organization not Being Limited to Workplace
- 5.2 Market Restraints
- 5.2.1 Legacy Applications, Infrastructure, and Operating Systems Not Likely to Adopt Zero Trust Model
6 MARKET SEGMENTATION
- 6.1 By Deployment
- 6.1.1 On-premise
- 6.1.2 Cloud
- 6.2 By Organization Size
- 6.2.1 Small and medium Enterprises
- 6.2.2 Large Enterprises
- 6.3 By End-user Industry
- 6.3.1 IT and Telecom
- 6.3.2 BFSI
- 6.3.3 Manufacturing
- 6.3.4 Healthcare
- 6.3.5 Energy and Power
- 6.3.6 Retail
- 6.3.7 Government
- 6.3.8 Other End-user Industries
- 6.4 By Geography
- 6.4.1 North America
- 6.4.2 Europe
- 6.4.3 Asia Pacific
- 6.4.4 Rest of the World
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles*
- 7.1.1 Cisco Systems Inc.
- 7.1.2 Palo Alto Networks, Inc.
- 7.1.3 Vmware, Inc.
- 7.1.4 Broadcom Inc. (Symantec Corporation)
- 7.1.5 Microsoft Corporation
- 7.1.6 IBM Corporation
- 7.1.7 Google LLC (Alphabet Inc.)
- 7.1.8 Check Point Software Technologies Ltd
- 7.1.9 BlackBerry Limited
- 7.1.10 Akamai Technologies Inc.
- 7.1.11 DELINEA (Centrify Corporation)
- 7.1.12 Okta Inc.
- 7.1.13 Fortinet, Inc.
- 7.1.14 Sophos Ltd.
- 7.1.15 Cyxtera Technologies Inc.













