 |
市場調查報告書
商品編碼
1403056
雲端入侵防禦軟體 -市場佔有率分析、產業趨勢與統計、2024-2029 年成長預測Cloud Intrusion Protection Software - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts 2024 - 2029 |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
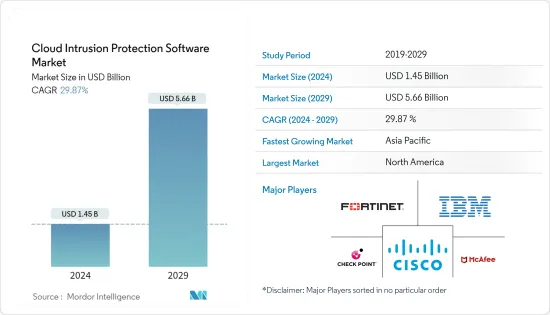
雲端入侵防禦軟體市場規模預計到 2024 年為 14.5 億美元,預計到 2029 年將達到 56.6 億美元,在預測期內(2024-2029 年)複合年成長率為 29.87%。
主要亮點
- 許多企業已經開始實施雲端服務,雲端服務的使用正在廣泛領域迅速擴展。軟體漏洞已成為一個嚴重的問題,隨著新軟體更新的發布以阻止新威脅,一些組織正在努力修補其環境。
- 雲端入侵防禦軟體解決方案透過阻止試圖利用已知漏洞(包括 CVE資料庫中包含的漏洞)的流量來保護雲端基礎的應用程式和本機應用程式。雲端入侵防禦軟體可以防範新漏洞,無需安全和 IT 團隊的手動干預,從而減輕了手動修補公司伺服器、使用者系統和雲端應用程式的負擔。
- 據 IC3 稱,近年來網路釣魚攻擊大幅增加。到 2022 年,將有超過 30 萬人成為此類攻擊的受害者。網路釣魚攻擊有型態。最常見的類型是大量網路釣魚、簡訊詐騙和商業電子郵件詐騙(BEC)。 2022 年,85% 的接受調查的全球公司表示,他們經歷過重大網路釣魚攻擊,近四分之三的公司表示,他們是網路釣魚詐騙的受害者。
- 不斷增加的網路威脅和駭客攻擊正在推動企業和個人用戶使用雲端入侵防禦軟體。由於商業網路入侵事件的增加,IT 在網路安全方面的支出也在增加。入侵偵測和防禦已成為 IT 公司保護自己免受針對性攻擊的最重要手段。
- 如今,保護企業免受駭客攻擊已成為 IT 公司的主要關注點。但該軟體因多次檢查、偵測、偵測而導致網路效能下降,導致市場需求流失。
- 網路威脅正在上升,由於 COVID-19 導致遠距連線和在家工作的增加,網路威脅不斷加劇。因此,各行業對網路安全解決方案的需求不斷增加。組織投資先進的網路安全技術,例如防火牆、入侵偵測和預防系統以及加密工具,以保護網路和系統免受網路威脅。
雲端入侵防禦軟體市場趨勢
電訊和資訊技術預計將呈指數級成長
- 雲端入侵防禦系統擴大被電訊業採用,該行業服務於市場上的所有其他行業。過去十年,隨著技術進步和現代連接系統採用的增加,汽車、零售、能源和電力、政府服務、IT 部門和其他技術行業等行業對通訊服務的需求不斷成長。實現了。
- 通訊業是各行各業順利運作的重要連結。隨著雲端服務的出現,對通訊的依賴增加。通訊業和 IT 產業已經合併,以提供更好的營運。目前,IT產業發揮重要作用。隨著產業向雲端化和自動化邁進,IT系統被部署來支援業務,通訊業正在提供連接和通訊服務以促進整個系統的運作。
- 此外,隨著5G、人工智慧、物聯網等技術的快速發展,需要防止資料外洩並保護跨網路的資料。此外,合作夥伴關係和產品創新等市場參與企業的策略和開拓預計將在預測期內推動細分市場的成長。
- 例如,2022 年 9 月,VMware 在拉斯維加斯 MWC 上宣布推出多種新穎產品和合作夥伴關係,旨在加速 RAN、5G 核心和邊緣部署和生命週期管理。其中包括 VMware 電信雲端平台生態系統的擴展型態,該系統允許調節器平面和工作節點池獨立昇級,以透過東西向網路流量的 IDPS 保護 5G 網路。 VMware也表示,它擁有一個不斷成長的合作夥伴生態系統,擁有超過275個雲端和虛擬網路功能,包括Mavenir的Joined Packet Core,以協助加速網路服務的使用。
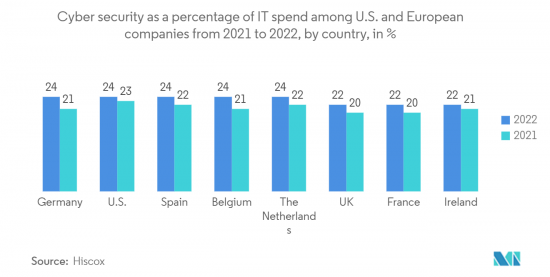
- 由於網路攻擊的增加,企業正在增加IT基礎設施的支出,以防止資料外洩和資料竊取。由於 IT 和電訊在網路連接中發揮關鍵作用,因此 IT 和電訊行業的網路安全支出預計將高於其他行業。根據 Hiscox 2022 年網路就緒報告,德國企業 IT 網路安全支出比例從 2021 年的 21% 增加到 2022 年的 24%。網路攻擊為企業帶來的風險顯著增加,導致預防投資增加。
北美對市場成長做出了重大貢獻
- 北美市場是雲端入侵防禦軟體軟體公司的重點市場。北美市場對雲端入侵防禦軟體的貢獻最高。大公司的存在、網路攻擊頻率的增加以及託管伺服器數量的增加等因素正在推動該地區的市場發展。
- 此外,近年來美國組織和個人面臨的網路威脅和攻擊總數激增,使得網路安全成為越來越重要的領域。根據身分盜竊資源中心的數據,2022 年美國發生的資料外洩總數約為 1,802 起。同時,到 2022 年,超過 4.22 億人受到資料外洩的嚴重影響,包括資料外洩、資料外洩和外洩。
- 到 2021 年,該國針對手動程度較低、自動化程度較高的組織的網路釣魚和勒索軟體攻擊也將增加。根據 Emsisoft 2023 年 1 月發布的年終報告,儘管美國政府努力遏制威脅,但 2022 年學校遭受的網路攻擊數量將與 2021 年大致相同。網路威脅和駭客攻擊預計將推動北美雲端入侵者防護軟體市場的發展。
- 2023 年 2 月,Windstream Enterprise 宣布推出北美首個完全託管的安全服務邊緣 (SSE) 解決方案。 Cato Networks 的 Windstream Enterprise SSE 提供完整的內建安全功能集合,包括入侵防禦系統(入侵防禦軟體),可監控網路流量並阻止惡意內容,防止漏洞利用、遷移,抵禦各種網路威脅,包括勒索軟體和其他基於網路的攻擊。
- 2023 年 6 月,AT&T Cybersecurity 與 Vertek Corporation 合作,為大中型企業提供統一安全管理 (USM)。 Vertek 最先進的安全營運中心 (SOC) 為希望保護其業務免受威脅的企業客戶提供預測性主動緩解和威脅偵測服務。 Vertek 使用 AT&T Cybersecurity 的 USM Anywhere 解決方案作為 Vertek 24/7/365 SOC(一個全面的多層網路安全平台)的一部分。它由即時入侵偵測和回應監控、行為監控、深度漏洞掃描、SIEM 和日誌管理組成,為客戶在不斷變化和發展的環境中提供無與倫比的威脅防護。
雲端入侵防禦軟體產業概況
由於網路攻擊的增加,雲端入侵防禦軟體市場高度分散。為了維持市場佔有率,許多公司正在升級現有的產品系列,而新參與企業則繼續開拓市場並推出適合其需求的產品。這個充滿活力的市場的主要企業包括思科系統公司、IBM公司、Fortinet公司、Check Point軟體技術有限公司和賽門鐵克公司。
2023 年 6 月,領先的 3D LiDAR 解決方案供應商 Quanergy Solutions, Inc. 與著名的基於服務的系統整合公司 Convergint 建立了策略合作夥伴關係。該合作夥伴關係旨在為公共產業部門提供先進的周界入侵偵測功能。
2022 年 10 月,Moxa 在其 EDR-G9010 系列受保護路由器上推出了 IDS/入侵防禦軟體功能,以及 MXsecurity 開發的安全管理軟體。產品系列中的這項新增功能提供了具有 NAT、防火牆、交換器和 VPN 功能的安全路由器,以增強專門建置的管理和網路安全解決方案。 EDR-G9010系列配備IDS/入侵防禦軟體,變身為下一代工業防火牆,具有增強的威脅防禦和偵測功能,進一步保護關鍵基礎架構免受網路安全威脅。
2022 年 12 月,Corelight 宣布對其增強型入侵偵測軟體 (IDS) 訂閱進行重大軟體增強。這些增強功能使安全團隊能夠無縫整合安全工具並提高其有效性。這是透過產生警報並結合必要的證據來促進分類、檢驗和補救工作來實現的。此外,這些改進使客戶能夠以 Corelight 更先進的產品取代傳統的 IDS 解決方案。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3 個月分析師支持
目錄
第1章簡介
- 研究成果
- 研究場所
- 調查範圍
第2章調查方法
第3章執行摘要
第4章市場洞察
- 市場概況
- 產業價值鏈分析
- 產業吸引力-波特五力分析
- 新進入者的威脅
- 買家/消費者的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭公司之間的敵對關係
- 技術簡介
第5章市場動態
- 市場促進因素
- 網路威脅和駭客攻擊嘗試
- 增加網路安全方面的 IT 支出
- 市場抑制因素
- 偵測誤報和漏報
- 由於多次檢查導致網路效能下降
第6章市場區隔
- 按服務
- 諮詢
- 管理服務
- 設計與整合
- 培訓和教育
- 按行業分類
- 電訊/資訊技術
- 銀行/金融服務
- 油和氣
- 製造業
- 醫療保健
- 政府機關
- 旅遊/交通
- 零售業
- 娛樂和媒體
- 其他行業
- 地區
- 北美洲
- 歐洲
- 亞太地區
- 拉丁美洲
- 中東/非洲
第7章競爭形勢
- 公司簡介
- Cisco Systems Inc.
- IBM Corporation
- Fortinet Inc.
- Check Point Software Technologies Ltd
- HP Inc.
- McAfee Inc.(Intel Corporation)
- Dell Inc.
- Trustwave Corporation
- AlienVault Inc.(AT&T Cybersecurity)
- Broadcom Inc.(Symantec Corporation)
第8章投資分析
第9章 市場機會及未來趨勢

The Cloud Intrusion Protection Software Market size is estimated at USD 1.45 billion in 2024, and is expected to reach USD 5.66 billion by 2029, growing at a CAGR of 29.87% during the forecast period (2024-2029).
Key Highlights
- The use of cloud services is growing rapidly in a broad range of areas as more companies are beginning to implement cloud services. Software vulnerabilities have become a serious problem, and several organizations struggle to patch their environments when new software updates are released to block emerging threats.
- Cloud IPS solutions protect cloud-based and on-premises applications by blocking traffic that attempts to exploit known vulnerabilities, including those contained in the CVE database. This reduces the burden of manually patching enterprise servers, user systems, or cloud applications, as Cloud IPS protects against new vulnerabilities without requiring manual intervention by security or IT teams.
- According to IC3, Phishing attacks have significantly increased in recent years. In 2022, more than 300,000 people fell victim to such attacks. Phishing attacks come in many forms. The most common types are bulk phishing, smishing, and business email compromise (BEC). In 2022, 85% of global organizations surveyed stated that they had experienced a major phishing attack, and almost three in four said they were affected by a smishing scam.
- The increasing number of cyber threats and hacking attempts drive companies and individual users to use cloud intrusion protection software. In addition, considering the increasing number of intrusion incidents in business networks, there has been increased IT spending on network security. Intrusion detection and prevention have been the most important hacks for IT companies to protect themselves from targeted attacks.
- Saving a company from hackers has become a major effort by IT companies these days. However, network performance loss owing to several checks and false positives and false negative detections by this software can lead to a loss of market demand.
- Cyber threats have increased, exacerbated by increased long-distance connectivity and working from home due to COVID-19. As a result, the demand for cybersecurity solutions is increasing across various industries. Organizations invest in advanced cybersecurity technologies such as firewalls, intrusion detection and prevention systems, and encryption tools to protect their networks and systems from cyber threats.
Cloud Intrusion Protection Software Market Trends
Telecom and Information Technology Expected to Grow Exponentially
- Cloud intrusion protection systems are being increasingly adopted in the telecom industry, which serves every other industry in the market. With technological advancements and the increasing adoption of modern connectivity systems, the demand for communication services in industries such as automotive, retail, energy and power, government services, the IT sector, and other industries employing technology has seen incremental growth over the past decade.
- The telecom industry is a critical link for every industry to operate without interruptions. With the advent of cloud services, the dependence on communication is growing. The telecom and IT industries have merged to provide better operations. The IT industry nowadays plays a major role. With industries moving toward cloud and automation, they are increasingly deploying IT systems to support operations and telecom industries to provide connectivity and communication services to facilitate the working of the whole system.
- Moreover, with the prompt growth in technology such as 5G, AI, and IoT, it is necessary to prevent data breaches and protect the data across the network. Moreover, strategies and development by market players, such as partnerships and product innovations, are expected to drive segment growth during the forecast period.
- For instance, in September 2022, VMware launched various novel products and partnerships at MWC Las Vegas, intended to hasten RAN, 5G core, edge deployments, and lifecycle managing. This includes VMware, an extended form of its Telco Cloud Platform Ecosystem so workers can upgrade the regulator plane and worker node pools distinctly and protect their 5G networks with IDPS for east-west network traffic. VMware also stated that it can speed up the utilization of network services owing to the growing partner ecosystem of over 275 cloud- and virtual-network functions, including Mavenir's Joined Packet Core.
- The increasing number of cyberattacks has boosted businesses to increase their IT infrastructure spending to prevent data breaches and data theft. As IT and telecom hold a significant stake in cyber connectivity, the IT and telecom industry's cybersecurity spending is expected to be higher than the other industries. As per Hiscox Cyber Readiness Report 2022, the share of companies' IT spending on cyber security in Germany increased from 21% in 2021 to 24% in 2022. The risk to companies of cyber-attacks is expanding significantly, hence the expanded investment in prevention.

North America is the Major Contributor to the Market Growth
- The North American market has been the focus of cloud IPS software companies. The North American market is the highest contributor to cloud IPS software. Factors such as the presence of large enterprises, the growing frequency of cyber-attacks, and the increasing number of hosted servers are driving the market in the region.
- Moreover, cybersecurity has become an increasingly important area of focus in the United States in recent years due to the surge in the total count of cyber threats and attacks that organizations and individuals face. As per the Identity Theft Resource Center, in 2022, the total number of data compromises in the United States stood at around 1802 cases. Meanwhile, over 422 million individuals were greatly affected in 2022 by data compromises, including leakage, data breaches, and exposure.
- The country also marks an increase in phishing and ransomware attacks targeting organizations with less manual effort and high automation by 2021. According to Emsisoft's year-end report published in January 2023, the number of cyberattacks on schools in 2022 is almost the same as in 2021, despite the US government's efforts to contain the threat. Cyber threats and hacking efforts are expected to drive North America's cloud intruder protection software market.
- In February 2023, Windstream Enterprise announced the first fully managed Security Service Edge (SSE) solution in North America, powered by Cato Networks. Windstream Enterprise SSE, powered by Cato Networks, offers a complete collection of built-in security features, including an Intrusion Prevention System (IPS) to monitor network traffic and block malicious content, protect against a variety of cyber threats such as exploits, migrations, ransomware, and other network-based attacks.
- In June 2023, AT&T Cybersecurity and Vertek Corporation partnered to deliver Unified Security Management (USM) to mid-sized and large businesses. Vertek's cutting-edge Security Operations Center (SOC) provides predictive and proactive mitigation and threat detection services to enterprise customers looking to protect their businesses against threats. Vertek uses AT&T Cybersecurity's USM Anywhere solution as part of Vertek's 24/7/365 SOC, a comprehensive multi-layered cybersecurity platform. It comprises real-time intrusion detection and response monitoring, behavioral monitoring, in-depth vulnerability scanning, SIEM, and log management to offer customers unparalleled protection against the threat, which is an ever-changing and evolving environment.
Cloud Intrusion Protection Software Industry Overview
The market for cloud intrusion protection software has become highly fragmented due to the increasing number of cyber attacks. To retain their market share, many companies are upgrading their existing product portfolios while new players continue to explore the market and launch products tailored to their needs. Some of the key players in this dynamic market include Cisco Systems Inc., IBM Corporation, Fortinet Inc., Check Point Software Technologies Ltd, and Symantec Corporation.
In June 2023, Quanergy Solutions, Inc., a leading provider of 3D LiDAR solutions, formed a strategic partnership with Convergint, a prominent service-based systems integration company. This collaboration aims to deliver advanced perimeter intrusion detection capabilities for the utility sector.
In October 2022, Moxa introduced IDS/IPS functionality to its EDR-G9010 Series protected routers, along with the MXsecurity-developed security management software. This addition to their product portfolio enhances the purpose-built management and cybersecurity solutions, offering a secure router equipped with NAT, firewall, switch, and VPN functionality. The inclusion of IDS/IPS transforms the EDR-G9010 Series into a next-generation industrial firewall, bolstered with threat prevention and detection capabilities, providing added protection to critical infrastructure against cybersecurity threats.
In December 2022, Corelight unveiled significant software enhancements for its enhanced intrusion detection software (IDS) subscription. These enhancements allow security teams to seamlessly integrate security tools and increase their effectiveness. This is achieved by generating alerts combined with the necessary evidence to facilitate triage, validation, and remediation efforts. Furthermore, these improvements empower customers to replace legacy IDS solutions with Corelight's more advanced offerings.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Deliverables
- 1.2 Study Assumptions
- 1.3 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Threat of New Entrants
- 4.3.2 Bargaining Power of Buyers/Consumers
- 4.3.3 Bargaining Power of Suppliers
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Technology Snapshot
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Cyber Threats and Hacking Attempts
- 5.1.2 Increased IT Spending on Network Security
- 5.2 Market Restraints
- 5.2.1 Detection of False Positives and False Negatives
- 5.2.2 Loss of Network Performance Due to Multiple Checks
6 MARKET SEGMENTATION
- 6.1 By Service
- 6.1.1 Consulting
- 6.1.2 Managed Service
- 6.1.3 Design and Integration
- 6.1.4 Training and Education
- 6.2 By Industry Vertical
- 6.2.1 Telecom and Information Technology
- 6.2.2 Banking and Financial Service
- 6.2.3 Oil and Gas
- 6.2.4 Manufacturing
- 6.2.5 Healthcare
- 6.2.6 Government
- 6.2.7 Travel and Transport
- 6.2.8 Retail
- 6.2.9 Entertainment and Media
- 6.2.10 Other Industry Verticals
- 6.3 Geography
- 6.3.1 North America
- 6.3.2 Europe
- 6.3.3 Asia-Pacific
- 6.3.4 Latin America
- 6.3.5 Middle East & Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Cisco Systems Inc.
- 7.1.2 IBM Corporation
- 7.1.3 Fortinet Inc.
- 7.1.4 Check Point Software Technologies Ltd
- 7.1.5 HP Inc.
- 7.1.6 McAfee Inc. (Intel Corporation)
- 7.1.7 Dell Inc.
- 7.1.8 Trustwave Corporation
- 7.1.9 AlienVault Inc. (AT&T Cybersecurity)
- 7.1.10 Broadcom Inc. (Symantec Corporation)









