 |
市場調查報告書
商品編碼
1273374
物聯網測試市場 - COVID-19 的增長、趨勢、影響和預測 (2023-2028)IoT Testing Market - Growth, Trends, and Forecasts (2023 - 2028) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
物聯網測試市場預計在預測期內以 32.34% 的複合年增長率增長。
由於採用創新技術的 IoT 測試導致針對不同應用的不同測試工具的利用率有所提高,因此預計該市場在預測期內將迅速擴大。
主要亮點
- 隨著智能手機和移動設備的普及以及互聯網的普及,近年來物聯網的發展取得了巨大的發展。 同樣的因素預計將在未來繼續推動對物聯網解決方案的需求。 這些設備的增加導致生成的數據增加。
- IoT 測試工具被廣泛用於幫助監控開源應用程序以及發送方和接收方之間的流量。 因此,物聯網測試工具連同物聯網解決方案,將有可能成為推動市場需求的關鍵因素。
- 此外,物聯網測試服務在測試智能組件和物聯網應用方面發揮著關鍵作用,可為最終用戶提供優質的體驗和服務。 物聯網測試使用實時智能和通信來確保連接網絡中硬件和軟件之間的完美協調。
- 越來越多的微服務部署主要推動了物聯網測試市場。 與傳統軟件開發相比,對 DevOps 的需求不斷增長,這提高了組織高速交付應用程序和服務的能力,這也推動了市場的擴張。
- 此外,越來越多地使用 IP(入口保護)測試來改進 IoT 設備以及 IoT 測試帶來的許多好處,例如網絡安全、連接設備的可用性、連接性和整體系統性能。消費者越來越意識到好處一直是主要的增長動力。
- 但是,隨著物聯網生態系統的發展,您可能會在測試過程中面臨擴展問題。 物聯網中微服務的測試自動化承諾通過允許每個微服務作為一個單獨的過程進行測試來降低測試大型架構的複雜性。 使用微服務進行物聯網測試的另一個優勢是能夠測試物聯網系統的可擴展性、可擴展性和集成性。
- 大流行期間對物聯網的需求不斷增加,增加了物聯網測試市場的增長機會。 由於 COVID-19 的爆發,全球供應鍊和對多種產品的需求經歷了中斷。 到 2020 年底,物聯網的採用將產生重大影響。 在後續階段,在醫療流行中採用物聯網技術以更好地進行信息協調和實時患者監控,極大地促進了物聯網檢測行業的複蘇。
物聯網測試市場趨勢
物聯網設備的增加可能會推動市場增長
- 對物聯網設備不斷增長的需求增加了對有效測試服務的需求。 在產品投放市場之前評估產品的質量至關重要。
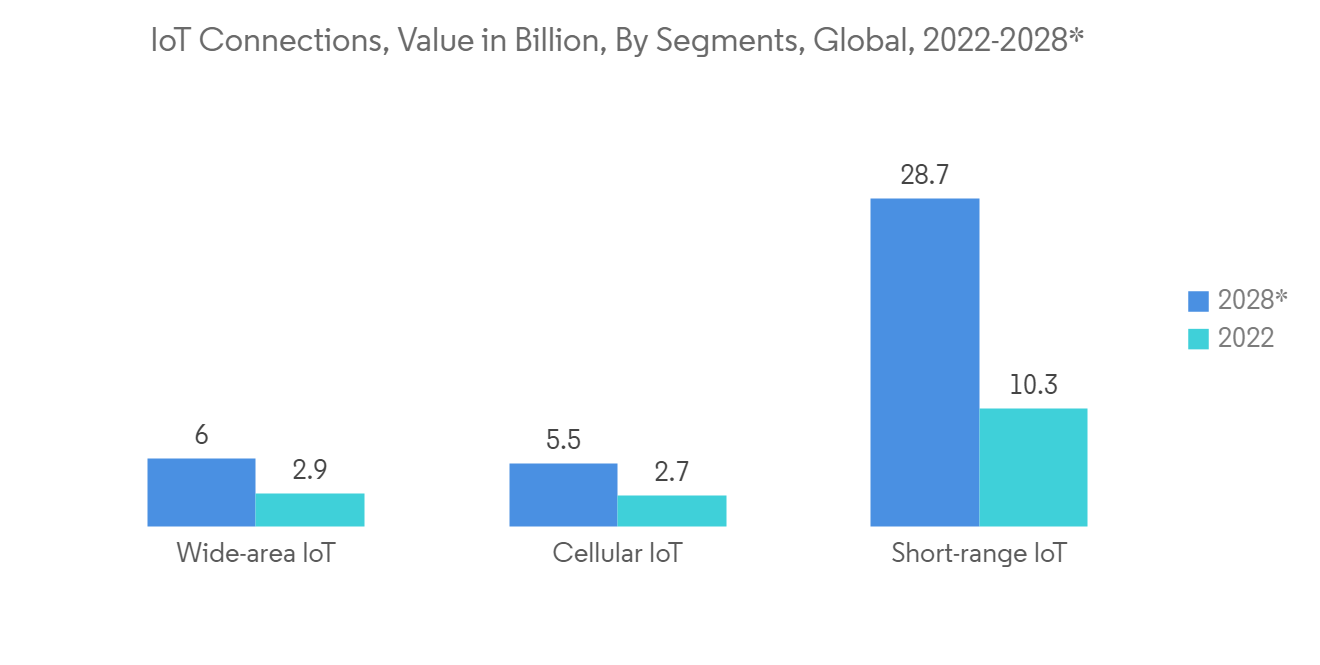
- 例如,根據愛立信的報告,到 2022 年,物聯網連接總量將約為 132 億日元。 預計這些技術將在 2021 年顯著增加連接設備的數量,到 2022 年底將達到約 5 億。 改進的網絡能力將通過實現 FDD 頻段上的大規模物聯網與 4G 和 5G 之間的頻率共享來促進大規模物聯網技術的發展。
- 託管物聯網測試服務提供商將新興技術視為未來幾年的重要商機。 在託管物聯網測試服務中,安全測試將比其他測試服務擁有更大的市場份額。
- 智慧城市計劃的日益普及正在激發物聯網在能源和公用事業、廢物管理和基礎設施方面的巨大潛力。 預計對支持物聯網的基礎設施的投資將突出對這些資產的安全測試服務的需求,這可能進一步推動這些領域對託管服務的需求。
- 此外,零售業中的智能設備和物聯網可幫助企業改善客戶體驗並提高轉化率,從而轉變商店的日常運營方式並增加該領域的託管服務。
- 出於這個原因,製造、醫療保健和政府機構等許多公司都敦促他們訂閱安全服務,而不是額外投資購買構建安全系統所需的硬件和軟件。
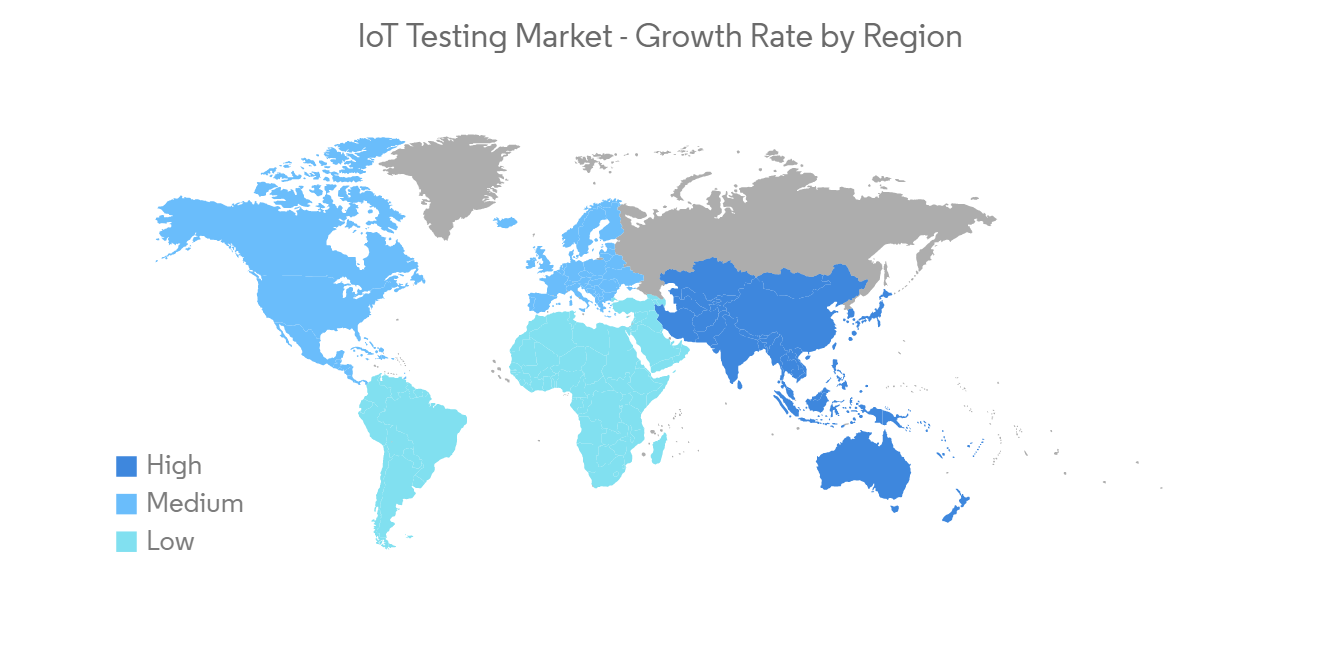
北美市場份額最大
- 按地區劃分,預計北美地區將佔據很大份額並主導物聯網測試市場。 該地區幾乎主導了一個可持續發展和成熟的經濟,這鼓勵了對研發活動的積極投資。 因此,它有助於物聯網、大數據、DevOps 和移動性等新技術的發展。
- 在美國,越來越多的消費者開始擁抱智能家居環境,物聯網也在北美地區進一步擴展。 根據斯坦福大學研究人員的一項研究,大約 66% 的北美家庭擁有至少一個物聯網設備,超過全球平均水平 40% 的四分之一。 在這些技術越來越受到黑客青睞的同時,這些智能家居的安全級別也在不斷提高。 物聯網的日益普及對測試服務市場的增長產生了重大影響。
- 此外,組織渴望將 IoT 技術整合到他們的流程中,這有望顯著促進 IoT 測試市場的增長。 例如,2022 年 10 月,拜登政府製作了一份關於改善和保護美國網絡安全措施的信息表,包括為物聯網設備製定網絡安全標準標籤。
- 此外,由於物聯網系統、測試技術和智能連接設備的應用不斷增加,該地區的市場正在擴大。 該地區的重大技術進步和所有業務部門對 5G 物聯網的需求推動了對物聯網測試解決方案的需求。
- 可靠的互聯網訪問的可用性以及製造業中互連設備的快速採用也有助於市場增長。 大量研發支出被投資於增強必要的網絡連接基礎設施和物聯網測試技術和服務,以支持該地區的市場份額。
- 此外,該地區出現了物聯網測試服務提供商,提供各種託管和專業服務,包括兼容性測試、試點測試、監管測試和升級測試。
物聯網測試行業概覽
物聯網測試市場競爭適中,由幾家重要參與者組成。 目前在市場上佔據主導地位的參與者包括 Novacoast, Inc.、Keysight Technologies, Inc.、Praetorian Security, Inc.、AFour Technologies Pvt. Ltd. (ACL Digital) 和 Apica Systems。 然而,物聯網測試解決方案提供商正專注於創造與競爭對手的差異化點,以維持全球市場的競爭格局。 一些參與者正在通過研發支出支持的新產品開發投資來擴大他們的產品供應。
2023 年 1 月,Happiest Minds Technologies Limited 以總計 11.1 億印度盧比(1350 萬盧比)的預付款和遞延股份對價收購了總部位於印度馬杜賴的知名 IT 服務公司 SMI 的 100% 股權。宣布它已經簽署了以美元收購該公司的最終協議。 SMI 擁有 400 多名離岸員工,年營業額約 900 萬美元。
2022 年 12 月,以設計為主導的工程服務、解決方案和數字化轉型公司 ACL Digital 宣布收購 AFour Technologies。 通過此次收購 AFour Technologies 公司,ACL Digitala 的產品工程和數字解決方案得到加強,並將加速其客戶的數字化轉型之旅。我們可以讓您的客戶更快地進行數字化轉型。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
內容
第一章介紹
- 調查假設和市場定義
- 本次調查的範圍
第二章研究方法論
第 3 章執行摘要
第 4 章市場洞察
- 市場概覽
- 行業價值鏈分析
- 行業吸引力 - 波特五力分析
- 供應商的議價能力
- 消費者的議價能力
- 新進入者的威脅
- 替代品的威脅
- 競爭公司之間的敵對關係
- 評估 COVID-19 對市場的影響
第 5 章市場動態
- 市場驅動因素
- 人們越來越擔心物聯網設備的安全性
- 物聯網設備數量增加
- 市場製約因素
- 物聯網設備的複雜性
- 缺乏統一的互操作性和互連標準
- 研究各種物聯網測試(數據完整性測試、功能測試、安全測試、性能測試、可用性測試、可靠性/可擴展性測試)
第 6 章市場細分
- 按服務類型
- 教授情緒化的
- 託管
- 按測試類型
- 功能測試
- 性能測試
- 網絡測試
- 兼容性測試
- 可用性測試
- 安全測試
- 最終用戶行業
- 零售
- 製造業
- 醫療保健
- 能源與公用事業
- IT/電信
- 其他最終用戶行業
- 地區
- 北美
- 歐洲
- 亞太地區
- 拉丁美洲
- 中東和非洲
第七章競爭格局
- 公司簡介
- IBM Corporation
- Apica Systems
- AFour Technologies Pvt. Ltd.(ACL Digital)
- Happiest Minds Technologies Pvt. Ltd
- Qualitest Group
- Praetorian Security, Inc.
- Saksoft Limited
- Keysight Technologies, Inc.
- Novacoast, Inc.
- Trustwave Holdings Inc.(Singtel)
- HCL Technologies Limited
第八章投資分析
第九章市場機會與未來趨勢
The IoT Testing market is expected to register a CAGR of 32.34% over the forecast period. The market is anticipated to expand faster during the forecast period due to the increased usage of various testing tools for various applications as a result of IoT testing employing innovative technology.
Key Highlights
- Due to the increasing adoption of smartphones and mobile devices, coupled with the growing internet penetration, the evolution of IoT has witnessed immense growth in recent years. The same factor is expected to continue driving the demand for IoT solutions in the future as well. The rise in these devices leads to increased data being generated.
- IoT testing tools are widely used for open-source applications and to help monitor the traffic between the sender and the receiver. Hence, IoT testing tools, along with IoT solutions, are likely to become a significant factor in driving the market demand.
- Moreover, IoT testing services play a vital role in testing smart components and IoT applications to offer end users superior quality experiences and services. IoT testing involves real-time intelligence and communication to ensure perfect harmony between hardware and software throughout the connected network.
- The increased deployment of microservices is primarily driving the market for IoT testing. The growing need for DevOps to improve an organization's capacity to provide apps and services at a high velocity compared to conventional software development is also accelerating the market's expansion.
- In addition, the increasing use of ingress protection (IP) testing for improved IoT devices and the growing consumer awareness of the many advantages offered by IoT testing, such as network security, the usability of connected devices, connectivity, system performance overall, etc., are significant growth-inducing factors.
- However, as the IoT ecosystem expands, it will likely face problems scaling the testing process. With microservices test automation in IoT, the complexity of testing a massive architecture is expected to reduce, as each microservice can be tested as a separate process. Utilizing microservices for IoT testing also offers the benefits of testing the IoT system's extensibility, scalability, and integrations.
- The growing demand for IoT during the pandemic increased the opportunities for the growth of the IoT testing market. Owing to the outbreak of COVID-19, the global supply chain and demand for multiple products have experienced disruption. The IoT adoption was significantly affected until the end of 2020. In later stages, the implementation of IoT technologies in healthcare during the epidemic for better information coordination and real-time patient monitoring significantly boosted the recovery of the IoT testing industry.
IoT Testing Market Trends
The Growing Number of IoT Devices may Drive the Market Growth
- The growing demand for IoT devices has boosted the requirement for effective testing services. Before a product is released onto the market, it is essential to assess its quality since even a small defect might significantly impact both the consumers and the company.
- For example, according to Ericsson's report, in 2022, the total IoT connections were reported to be valued at around 13.2 billion. These technologies enabled a significant increase in the number of connected devices in 2021, projected to reach about 500 million by the end of 2022. Increased network capabilities promote the development of Massive IoT technologies by enabling spectrum sharing between Massive IoT and 4G and 5G in FDD bands.
- Managed IoT testing service providers see emerging technology as a significant business opportunity for the next few years. Among managed IoT testing services, security testing will have a more substantial market share than other testing services.
- The increasing adoption of smart city concepts has evolved the great potential of IoT in energy and utilities, waste management, and infrastructure. The investment in IoT-enabled infrastructure is expected to accentuate the demand for security testing services for those assets, which may further foster the demand for managed services in these sectors.
- Moreover, smart devices and IoT in the retail sector help companies enhance the customer experience to drive more conversions, altering the day-to-day store operations and increasing the managed services in this sector.
- This encourages many companies operating in the manufacturing, healthcare, or government sectors to subscribe to security services instead of additionally investing in acquiring the hardware and software required to establish a security system.

North America Occupies the Largest Market Share
- By geography, the North American region is anticipated to hold a significant share, thereby dominating the IoT testing market. The region has substantial dominance over sustainable and well-established economies, empowering them to actively invest in R&D activities. Thus, it contributes to developing new technologies, such as IoT, Big Data, DevOps, and mobility.
- With rising consumers embracing the smart home environment in the United States, IoT is further expanding across the North American region. According to a study by Stanford University researchers, around 66% of North American households possess at least one IoT device, more than a quarter of the global average of 40%. Although these technologies are increasingly on the radar of hackers, the level of security of these smart homes has also been amplified. The increased adoption of IoT impacted the growth of the testing services market extensively.
- Moreover, organizations are keen to incorporate IoT technologies into their processes, which is expected to boost the IoT testing market's growth significantly. For instance, in October 2022, the Biden administration produced an information sheet on measures to improve and protect United States cybersecurity, including developing a cybersecurity standards label for IoT devices.
- Further, the market is growing in the region due to expanding IoT systems, testing technologies, and applications for smart, connected devices. The need for IoT testing solutions is driven by the region's significant technological advancements and demand for 5G IoT across all business sectors.
- The availability of highly reliable Internet access and the quick adoption of interconnected devices in manufacturing industries also contribute to the market's growth. Significant R&D expenditures are being made to enhance the necessary network connectivity infrastructure and IoT testing technologies & services, which support the region's market shares.
- Further, several IoT testing service providers across the region have emerged in the market, providing various managed or professional services, such as compatibility testing, pilot testing, regulatory testing, and upgrade testing.

IoT Testing Industry Overview
The IoT testing market is moderately competitive and consists of several significant players. Some players currently dominating the market in terms of market share include Novacoast, Inc., Keysight Technologies, Inc., Praetorian Security, Inc., AFour Technologies Pvt. Ltd. (ACL Digital), and Apica Systems. However, the IoT testing solution providers are focusing on creating a point of difference among their competitors to sustain the global market's competitive landscape. Several players are expanding their offerings through investments in new product development backed by research and development spending.
In January 2023, Happiest Minds Technologies Limited announced the signing of formal agreements to purchase 100% of SMI, a prominent IT services firm with headquarters in Madurai, India, for a total consideration of upfront and deferred equity consideration of INR 111 crores (USD 13.5 million). SMI has 400+ offshore workers and an annual sales run rate of about USD 9 Million.
In December 2022, ACL Digital, a player in design-driven engineering services, solutions, and digital transformation, declared the acquisition of AFour Technologies. ACL Digitala 's product engineering and digital solutions are strengthened by this purchase of the AFour Technologies company, and it will be able to speed up its clients' journeys toward digital transformation.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Suppliers
- 4.3.2 Bargaining Power of Consumers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Assessment of the Impact of COVID-19 on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increase in Security Concerns in IOT Devices
- 5.1.2 The Growing Number of IOT Devices
- 5.2 Market Restraints
- 5.2.1 Rising Complexity of IOT Devices
- 5.2.2 Shortage of Uniform Standards for Interoperability and Interconnection
- 5.3 Discussion on Various Types of IOT Testing (Data Integrity Testing, Functional Testing, Security Testing, Performance Testing, Usability Testing, Reliability & Scalability Testing)
6 MARKET SEGMENTATION
- 6.1 By Service Type
- 6.1.1 Professional
- 6.1.2 Managed
- 6.2 By Testing Type
- 6.2.1 Functional Testing
- 6.2.2 Performance Testing
- 6.2.3 Network Testing
- 6.2.4 Compatibility Testing
- 6.2.5 Usability Testing
- 6.2.6 Security Testing
- 6.3 End-user Industry
- 6.3.1 Retail
- 6.3.2 Manufacturing
- 6.3.3 Healthcare
- 6.3.4 Energy and Utilities
- 6.3.5 IT & Telecom
- 6.3.6 Other End-user Industries
- 6.4 Geography
- 6.4.1 North America
- 6.4.2 Europe
- 6.4.3 Asia-Pacific
- 6.4.4 Latin America
- 6.4.5 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 IBM Corporation
- 7.1.2 Apica Systems
- 7.1.3 AFour Technologies Pvt. Ltd. (ACL Digital)
- 7.1.4 Happiest Minds Technologies Pvt. Ltd
- 7.1.5 Qualitest Group
- 7.1.6 Praetorian Security, Inc.
- 7.1.7 Saksoft Limited
- 7.1.8 Keysight Technologies, Inc.
- 7.1.9 Novacoast, Inc.
- 7.1.10 Trustwave Holdings Inc. (Singtel)
- 7.1.11 HCL Technologies Limited










